OAuth2
Configuring the OAuth2 Plugin
To configure the OAuth2 plugin, first ensure the plugin has been enabled.
Navigate to the Plugins > Manage Plugins in the admin panel
Locate the OAuth2 Authentication plugin. It will likely be found on the Disabled Plugins tab unless it has been previously activated, in which case it can be found on the Enabled tab.
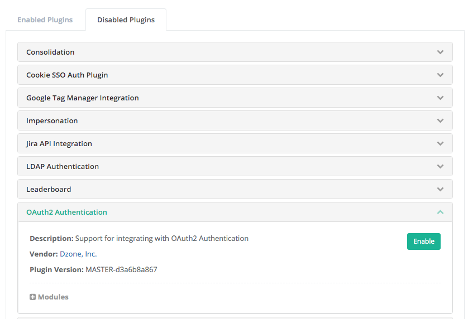
If it is disabled, click the down arrow on the right of the box to expand the section and then click the green Enable button.
Note: If you do not see the plugins section at the bottom of the left nav column in the administration section of the site, you will need to update the group membership for your user. Add your user to the Network Administrator Group to manage plugins.
Once you enable the OAuth plugin, navigate to Users and groups > Settings > OAuth2 Authentication.
The OAuth2 Authentication control panel should be displayed.
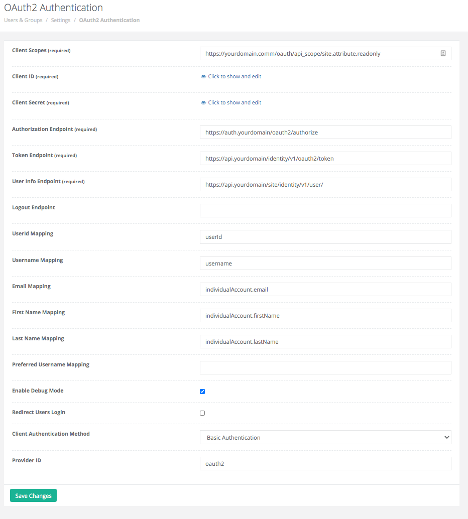
Client Scopes – One or more scopes may be specified on this line. Scopes limit an application’s access to a user’s account, and the access token issued will be limited to the scopes granted.
Client ID – Generated along with the Secret when registering the app. Typically, a hex string or text and hex combination.
Client Secret – Generated along with the Client ID when registering the app.
Authorization Endpoint – This is the URL for the authorization server
Token Endpoint – Token endpoint on the authorization server
User Info Endpoint – Endpoint that returns claims about the authenticated end-user. Client makes a request to the userinfo endpoint using an access token obtained from the token endpoint.
Logout Endpoint – Redirect users to a specified URL
Additional IDP Parameters - Optional configuration for parameters to be passed. Param1=value; Param2=value2
- UserId Mapping -The user’s IDP ID
- Username Mapping - The user’s IDP username
- Email Mapping - The user’s email address
- First Name Mapping - The user’s first name. If an IDP doesn’t have separate attributes for first name and last name, but it has the attribute of a full name, set the First Name Mapping to the full name attribute.
- Last Name Mapping -The user’s last name
- Preferred Username Mapping - The user’s preferred username. When the option is set and IDP returns a value, it will be used to replace the user’s IDP username.
Enable Debug Mode -The Boolean option to enable debug logging for SSO login. This may be checked during initial setup & debugging and should be unchecked once normal operation is achieved to reduce noise in the server logfile.
Redirect Users Login -The Boolean option to control the controller if you want to redirect /users/login.html to /users/social/login/{ providerId}.html.
Send welcome email to new users created by SSO - When checked, the welcome email is sent to users.
Client Authentication Method - The select option for the authenticate method for retrieving access token. The authentication method is configurable since authentication method is registered for IDP’s client_id. If no method is registered, the default method is client_secret_basic. (https://openid.net/specs/openid-connect-core-1_0.html#ClientAuthentication)
• Basic Authentication - Pass client credentials to the provider via HTTP Basic authentication
• Parameters - Pass client credentials to the provider as parameters instead of using HTTP Basic authentication
Provider ID - The option to set the provider ID. This option will allow to the admin to define their authentication service name for the OAuth2 provider. The default is "oauth2". For example, it allows to configure to "openidconnect" if using this plugin in place of openidconnect-auth plugin.
Updated 4 months ago
